More than 50% of the 90,310 hosts have been detected providing a Tinyproxy service on the internet that's vulnerable to a significant unpatched security hole in the HTTP/HTTPS proxy tool.
The issue, listed as CVE-2023-49606, carries a CVSS score of 9.8 out of a maximum of 10, per Cisco Talos, which described it as a use-after-free fault impacting versions 1.10.0 and 1.11.1, which is the newest version.
"A specially crafted HTTP header can trigger reuse of previously freed memory, which leads to memory corruption and could lead to remote code execution," Talos noted in an advisory last week. "An attacker needs to make an unauthenticated HTTP request to trigger this vulnerability."
In other words, an unauthenticated threat actor could submit a specially crafted HTTP Connection header to trigger memory corruption that can result in remote code execution.
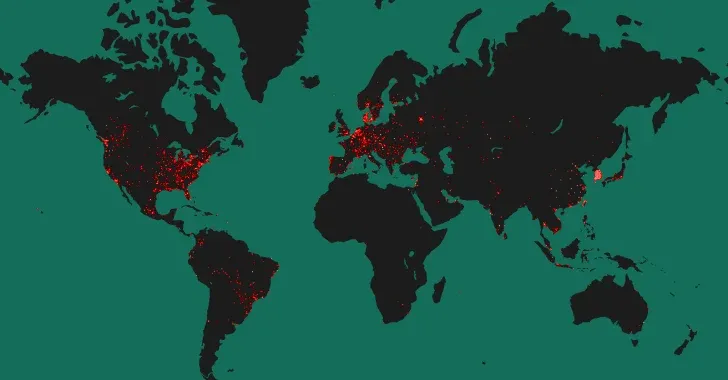
According to statistics given by attack surface management company Censys, of the 90,310 hosts exposing a Tinyproxy service to the public internet as of May 3, 2024, 52,000 (~57%) of them are running a vulnerable version of Tinyproxy.
A majority of the publicly-accessible hosts are located in the U.S. (32,846), South Korea (18,358), China (7,808), France (5,208), and Germany (3,680).
Talos, which reported the vulnerability to December 22, 2023, has also provided a proof-of-concept (PoC) for the flaw, outlining how the issue with processing HTTP Connection connections may be weaponized to induce a crash and, in some situations, code execution.
The maintainers of Tinyproxy, in a sequence of patches posted over the weekend, called out Talos for sending the report to a probable "outdated email address," adding they were made aware by a Debian Tinyproxy package maintainer on May 5, 2024.
"No GitHub issue was filed, and nobody mentioned a vulnerability on the mentioned IRC chat," rofl0r noted in a commit. "If the issue had been reported on Github or IRC, the bug would have been fixed within a day."
Users are recommended to update to the latest version as and when they become available. It's also suggested that the Tinyproxy service is not exposed to the public internet.